Which Process Is Used To Protect Transmitted Data In A Vpn
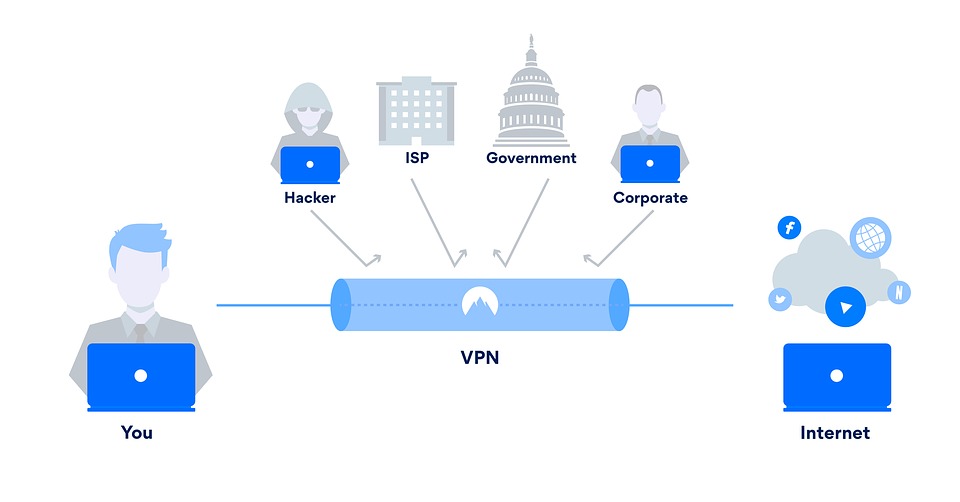
Introduced to the market nearly ii decades ago, Virtual Individual Networks (VPNs) are a uniquely enduring cornerstone of modern security. Most large organizations still use a VPN solution to facilitate secure remote admission, while millions of consumers rely on similar products to bolster their online privacy, secure public Wi-Fi connections, and circumvent site blocks.
By at present, well-nigh of us know that a VPN assigns the states a new IP address and transmits our online traffic through an encrypted tunnel. Only not all VPNs are created equally. Depending on the protocol in utilize, a VPN might have different speeds, capabilities, or fifty-fifty vulnerabilities.
Encryption protocols and ciphers are at the center of VPN engineering, determining how your 'secure tunnel' is actually formed. Each one represents a different solution to the problem of secure, private, and somewhat bearding browsing.
Though many of united states are aware of how a VPN generally works, information technology's common to get lost on the fine details of the engineering science due to the sheer complexity of the subject. This confusion is reinforced by the fact that many VPN providers can be slapdash to the bespeak of misleading when describing the blazon of encryption that they use.
This commodity volition provide a unproblematic point of reference for those who desire to explore the technologies driving their VPN service. Nosotros'll review dissimilar types of encryption, the principal VPN protocols available, and the common ciphers behind them.
In explaining the confusing array of terms unremarkably used by VPNs and other security products, you volition be in a stronger position to choose the most secure protocol and appraise the claims fabricated past VPN providers with a much more critical eye.
Types of VPN encryption
At a very basic level, encryption involves substituting letters and numbers to encode data and so that only authorized groups tin can access and understand it.
We now employ powerful algorithms called ciphers to perform encryption and decryption. These ciphers simply denote a serial of well-defined steps that can be followed repeatedly. The operation of a nothing unremarkably depends on a slice of auxiliary information called a key; without noesis of the key, it is extremely hard – if not incommunicable – to decrypt the resulting information.
When talking about encryption today, we by and large refer to a mixture of cipher and central-length, which denotes the number of 'bits' in a given key. For example, Blowfish-128 is the Blowfish cipher with a key length of 128 bits. Mostly speaking, a short central length means poor security equally it is more susceptible to violation by animal-force attacks.
A key length of 256 bits is the current 'gold standard'. This cannot be fauna-forced as it would take billions of years to run through all the possible flake combinations. There are a few key concepts in the world of encryption:
Symmetric-central
This is where the key for encryption and decryption is the same, and both communicating parties must possess the same key in lodge to communicate. This is the blazon of encryption used in VPN services.
Public-primal
Here, software is used to create sets of public and private keys. The public key is used to encrypt data, which is then sent to the owner of the private key. They and so apply this private key to decrypt the messages.

Network-based firewall service
Fully managed, cloud-based firewall providing continuous inspection and treatment of cyberspace traffic.
Learn more than
Handshake encryption (RSA)
Securely connecting to a VPN server requires the apply of public-key encryption through a TLS handshake. While a cipher secures your actual data, this handshake secures your connection.
This is typically done through the RSA (Rivest-Shamir-Adleman) algorithm, which has substantially been the foundation of net security for near 2 decades. Sadly, it now seems probable that RSA-1204 has been cracked by the NSA.
Today, near VPN services accept moved on from RSA-1024, but a small minority withal contain it. These services should be avoided. It's best to notice a service offer RSA-2048, which remains secure.
Secure Hash Algorithm (SHA)
The Secure Hash Algorithm (SHA) is used to cosign data and SSL/TLS connections. In this process, a unique fingerprint is created to validate the TLS certificate – that is, to check you're connecting to the server you lot're supposed to be. Without this, a hacker could re-route your traffic to their own server instead of your VPN provider'due south.
Protocols
VPN protocols represent the processes and instructions that VPN clients rely on to negotiate a secure connection betwixt a device and a VPN server. There are diverse different protocols ordinarily supported by commercial VPN services. Here are the principal protocols you need to know well-nigh:
SSL and TLS
Though non specifically a VPN protocol, this is the type of encryption most people are familiar with. It is used by both OpenVPN and all HTTPS-secured sites. Building on its predecessor – the SSL protocol (Secure Socket Layer) – TLS (Transport Layer Security) uses a mixture of symmetric and public-key encryption to secure network communications.
During this process, your web browser uses public-key encryption to communicate with a website's server and share the symmetric keys used to secure the transmitted data. The just effect here emerges when a website's server only uses ane private key to initiate all secure sessions. If this central is somehow compromised, a hacker can easily intercept and read whatsoever communications with that website. Thanks to Edward Snowden, we now know that the U.S. National Security Agency (NSA) has leveraged this vulnerability to get together swathes of seemingly secure information.
Fortunately, it'southward increasingly common for unique individual keys to be generated so disposed of later each TLS session. This is referred to equally Perfect Forward Secrecy or using 'ephemeral encryption keys'. Though nowhere nearly universal yet, the use of imperceptible keys is on the rise.
OpenVPN
This is the standard protocol used by well-nigh commercial VPN providers. It'due south widely configurable, very secure, and operational on nearly all VPN-capable devices.
OpenVPN is open up-source, which means its codebase is publicly available for inspection. Researchers can examination for vulnerabilities, substantiate security claims, and refine the product. It uses TLS protocols and the OpenSSL library in combination with a range of other tools to create a reliable and secure VPN connection. Custom OpenVPN applications are bachelor from commercial VPN providers, but the chief source lawmaking is created and developed by the OpenVPN Project.
OpenVPN encryption is comprised of two parts: information aqueduct and control channel encryption. The former consists of a cipher and hash authentication – both of which volition exist discussed later in this commodity – and is used to secure the data itself. The latter uses TLS encryption to secure the connexion between your computer and the VPN server, and consists of handshake encryption, naught, and hash authentication. For maximum security, both the information and command channel encryption should be as strong as possible.
It's important to be aware that some VPN providers don't use the aforementioned level of encryption on both of these channels. The stronger the encryption used, the slower the connection will be, so many providers employ weaker encryption on the data channel as a cheap shortcut to a faster connection. If you lot see a VPN service advertising its security merits, be certain to bank check that these claims apply to both channels.
OpenVPN works on both the UDP (User Datagram Protocol) port and TCP (Manual Control Protocol) port. The sometime transmits data packets without requiring confirmation of their arrival before transmitting the adjacent packet, resulting in lower latency. The latter – TCP – is the most mutual connection protocol on the web. When using this, a confirmation of the bundle's reception is required before the next information package can be sent.
Normal HTTPS traffic uses TCP port 443. Combining this port with OpenVPN means it's difficult to distinguish VPN connections from other connections usually used by email providers, online banking, and due east-commerce sites. This means OpenVPN is very hard to block, which is keen for those looking to use a VPN in highly-censored countries.
Ultimately, OpenVPN is the recommended VPN protocol under about circumstances. It is versatile, secure, and open source. While information technology has no real downsides, it'due south important that it is implemented well. This means use of strong encryption with Perfect Forward Secrecy.
IKEv2/IPsec
Internet Central Exchange version 2 (IKEv2) is a security association protocol that sets the foundation for a VPN connectedness by establishing an authenticated and encrypted connection between two parties. It was created past Microsoft and Cisco, and is natively supported by iOS, Windows vii and later, and Blackberry.
Every bit part of the IPsec internet security toolbox, IKEv2 uses other IPsec tools to provide comprehensive VPN coverage. This includes the Mobility and Multihoming protocol, which ensures the VPN stays connected equally the customer moves from one connection to some other. This makes IKEv2 a very dependable and stable protocol for mobile devices.
As part of the IPsec suite, IKEv2 works with almost leading encryption algorithms, which is testament to its security. That being said, the protocol is less efficient when trying to connect out of a highly censored country. What's more, IKEv2 uses a method called the Diffie Hellman process to exchange the keys it uses to secure your information. During the Snowden leaks, slides in an NSA presentation revealed they may have found a manner to break this procedure. Researchers working on a potential vulnerability estimated that, with hundreds of millions of dollars in calculating power investments, the NSA could potentially pause into every bit many equally 66% of IPsec connections.
Ultimately, IKEv2 is a reasonably secure and fast protocol. Mobile users in particular may adopt it to OpenVPN due to its stability throughout interrupted internet connections. For users of platforms like Blackberry, information technology'due south essentially the only option available.
L2TP/IPsec
Layer 2 Tunnelling Protocol (LT2P) is a proprietary Microsoft protocol that creates a connection between you lot and the other servers in your VPN. Like IKEv2, it relies on other tools in the IPsec suite to encrypt and authenticate your traffic as it can't perform these services itself. This protocol has a few convenient features, but various issues preclude information technology from outperforming its competitors.
Different other more sophisticated protocols, L2TP doesn't have whatsoever smart ways to bypass firewalls. Surveillance-minded system administrators use firewalls to block VPNs to forbid users from hiding their traffic. People using L2TP here are an piece of cake target as the protocol uses a relatively pocket-sized number of fixed ports.
L2TP encapsulates data twice; while this can be useful for some applications, information technology makes it slower compared to other protocols that encapsulate information only once.
Like IKEv2, LT2P is typically used with IPsec. Some VPN providers have been known to administer this combination poorly, often using pre-shared keys that are bachelor to download online. While these are solely used for authentication and not decryption, a malicious actor could use this key to imitate a VPN server.
For those willing to overlook these bug, LT2P/IPsec is a good choice for non-critical use given the number of dissimilar encryption protocols it can accept and the fact it is natively supported past so many platforms. This is especially true for legacy devices that exercise not support OpenVPN.
SSTP
Secure Socket Tunnelling Protocol (SSTP) is a proprietary Microsoft-owned protocol based on SSL iii.0. Like OpenVPN, it supports AES-256 and tin can use TCP port 443. SSTP offers near of the advantages of OpenVPN but is primarily simply for Windows.
SSTP's shut association with Microsoft means you lot can be confident that whatever device using Vista or a later Windows Os will either support SSTP or take it built-in. Likewise, you may be able to receive support from Microsoft if you take problems in implementing the protocol.
That being said, SSTP is not open-source. It is therefore not possible to analyse or refute suggestions of backdoors and vulnerabilities, or for security researchers to test for potential weaknesses. Microsoft has been known to cooperate with institutions like the NSA in the past, so some suspect the system may include backdoors that allow these agencies to track targeted users. For this reason, the risks of its shut integration with Windows largely outweigh any benefits.
WireGuard
WireGuard is a relatively new tunnelling protocol that seeks to offer better performance and faster speeds than OpenVPN.
The protocol is designed to resolve some of the negative problems normally associated with IPsec and OpenVPN: frequent disconnections, circuitous setup for users looking to manually configure, extended reconnection times, and heavy codebases which can make it hard for researchers to spot bugs.
WireGuard aims to surpass traditional protocols by using more modern ciphers. It's codebase is only 4000 lines – around 1% of OpenVPN's and IPsec's.
Though it's still in development, preliminary tests suggest that WireGuard is fast, secure and reconnects instantaneously. Information technology has yet to fully 'prove itself', only a ascension number of VPN services are being applauded for including it with their clients, including IVPN and Mullvad VPN.
PPTP
Designed to create a VPN over dial-upwardly connection, the Point-to-Signal Tunnelling Protocol (PPTP) is an erstwhile VPN protocol developed in 1999 by a team funded by Microsoft.
It however retains some positives: it's widely compatible, doesn't require extra software, and is quite fast.
The biggest issue is with security. PPTP is proven to exist insecure and very easy to suspension. PPTP traffic is also easy to obstruct as it depends on the GRE protocol which is easily stumped past a firewall. Avoid using PPTP unless it is totally necessary for non-critical use.
Choosing a VPN protocol
Information technology's best to opt for OpenVPN where bachelor, peculiarly when setup is handled by a third-party app. L2TP/IPsec is probably the most widely used alternative and offers the adjacent-best in terms of security. SSTP is a reasonable pick for Windows users that trust proprietary tech from Microsoft, while IKEv2 is a fast alternative for the few devices – specially mobile – that support it. PPTP should only be used as a very last resort.
Ciphers
While key length refers to the amount of numbers or '$.25' involved, a cipher is the formula or algorithm used to actually bear out the encryption. The strength of a cipher is dependent on both the fundamental length and the forcefulness of these formulas.
Information technology's worth mentioning that a larger key length means more calculations are involved, then more processing power is required. This affects how fast data can be encrypted and decrypted. Commercial VPN providers must therefore negotiate the residuum between security and usability when choosing an encryption scheme.
AES
The Advanced Encryption Standard (AES) is a symmetric-primal cipher established in 2001 by The National Plant of Standards and Technology (NIST). Information technology essentially represents the 'gilt standard' of the contemporary VPN industry. Though AES-128 is considered secure, AES-256 is preferable as information technology offers stronger protection.
Blowfish
Blowfish is the default cipher used in OpenVPN, though it can exist configured to others. The most commonly used version is Blowfish-128, only it theoretically can range from 32 to 448 bits.
The cipher is generally secure but does sport some vulnerabilities. It should more often than not only be chosen when AES-256 is unavailable.
Camellia
This zippo is similar to AES. The essential difference is that Camellia is not certified by NIST, the American organization that designed AES.
There is definitely an statement for trusting a zip that doesn't sport strong ties to the The states government. That being said, Camellia is very rarely available in commercial VPN software, and hasn't been vetted as thoroughly AES.
Securing your VPN connectedness
The types of encryption, protocols, and ciphers above should assist to strengthen your understanding of what drives and secures your VPN connection. If you're choosing a consumer or enterprise VPN provider, consider these concepts when assessing the claims that providers make.
Be sceptical. It's not uncommon to see VPN services advertise their apply of 'armed services-course' 256-chip AES OpenVPN encryption; in reality, this doesn't reveal all that much. While AES-256 might be a potent aught, your data only won't be secure if other parts of the encryption suite are weak. Consider their use of hash authentication, perfect forward secrecy, and the difference in encryption settings on both the data and control channels.
Which Process Is Used To Protect Transmitted Data In A Vpn,
Source: https://cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers
Posted by: lightliess1983.blogspot.com


0 Response to "Which Process Is Used To Protect Transmitted Data In A Vpn"
Post a Comment